Please note that the procedures outlined in this guide pertain to connecting a GCS bucket and LABELLERR within the same Google Cloud account.
Quick Reference
GCS URI Format
GCS Path Format
Required Permissions Summary
- Import (Read)
- Export (Write)
| Permission | Purpose |
|---|---|
storage.objects.get | Read files from bucket |
storage.objects.list | List files in bucket |
storage.buckets.get | Get bucket metadata |
storage.buckets.update | Update bucket settings (CORS) |
S3 vs GCS Comparison
| Feature | AWS S3 | Google Cloud Storage |
|---|---|---|
| URI Format | s3://bucket/path/ | gs://bucket/path/ |
| Authentication | Access Key + Secret Key | Service Account JSON |
| Import Permissions | 5 permissions | 4 permissions |
| Export Permissions | +2 permissions | +2 permissions |
| CORS Setup | Via IAM policy or manual | Via bucket settings |
Prerequisites
Role Creation
Go to the IAM & Admin Console: Add Permissions:
Add Permissions:
- Open the Google Cloud Console
- Navigate to IAM & Admin > Roles
- Click on + CREATE ROLE
- Enter a Title, ID, and Description for the role
- Click CONTINUE

- In the Permissions section, add the necessary permissions
storage.buckets.getstorage.buckets.updatestorage.objects.getstorage.objects.list
- Click CONTINUE
- Review the role details
- Click CREATE

Service Account Creation
Go to the Service Accounts Console: Create a Service Account:
Create a Service Account: Grant Users Access to this Service Account (Optional):
Grant Users Access to this Service Account (Optional):
- In the Google Cloud Console, navigate to IAM & Admin > Service Accounts

- Click on + CREATE SERVICE ACCOUNT
- Enter a Service account name and Description
- Click CREATE AND CONTINUE
- In the Grant this service account access to project section, add the role created in the previous step
- Click CONTINUE

- If needed, add users who can manage this service account
- Click DONE
Generate and Download Service Account Key
Select Service Account: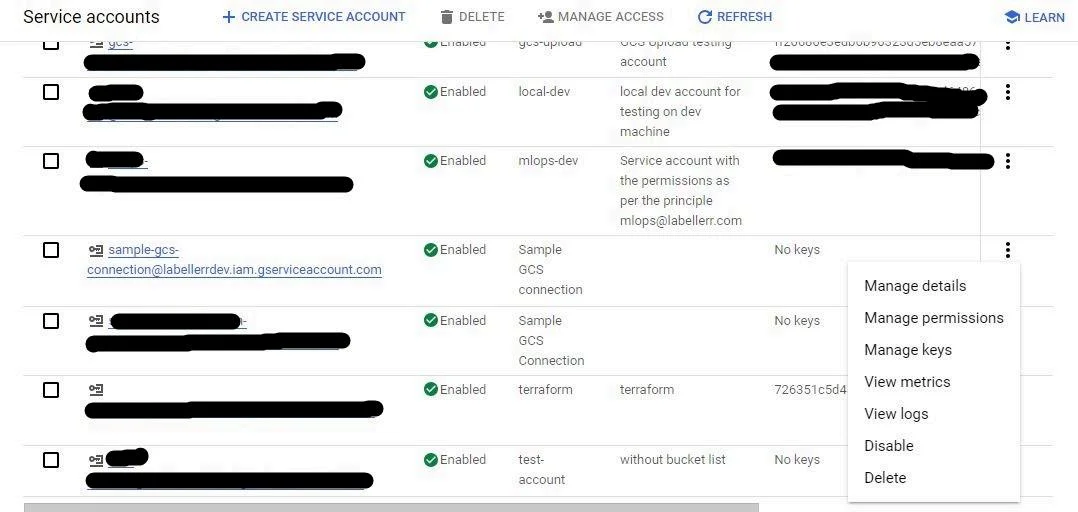 Create Key:
Create Key: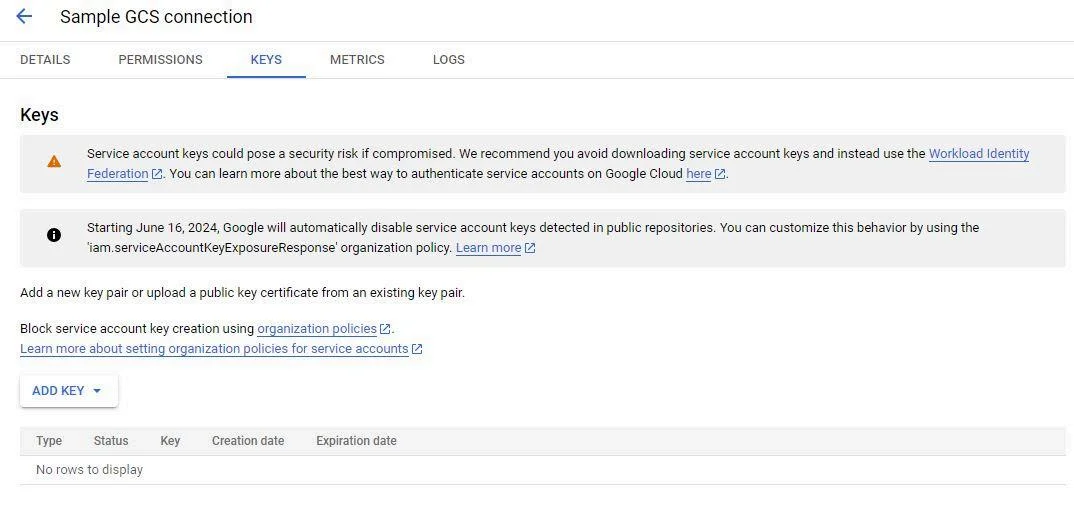
- In the Service Accounts console, find the service account you created
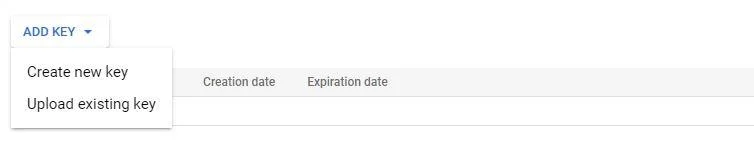
- Click the ⋮ (three vertical dots) next to the service account and select Manage keys

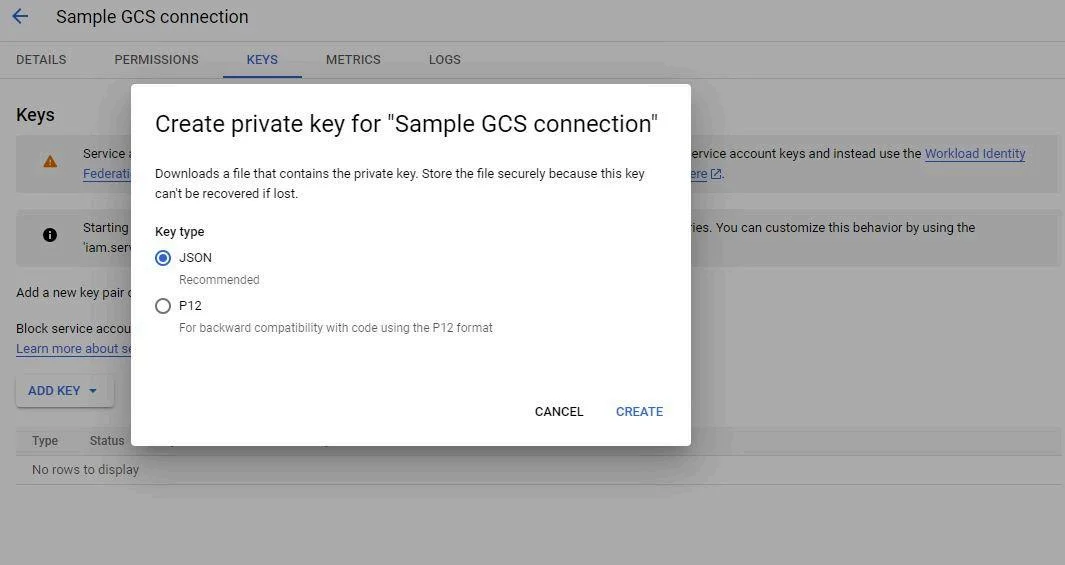
- Click ADD KEY > Create new key



- Click CREATE
- A JSON key file will be downloaded. Keep this file secure as it contains the credentials needed to access the GCS bucket
Assign IAM Policy to GCS Bucket
- Go to the Cloud Storage Console: Navigate to Cloud Storage > Buckets in the Google Cloud Console
- Select Your Bucket: Click on the name of your private bucket. You will see the bucket details, including its Name, Location, and other information
- Open Permissions: Click on the Permissions tab
- Add Member:
- Click ADD
- In the New members field, enter the service account email
- Select the role you created earlier
- Click SAVE
Use the Labellerr tool to Access the GCS Data
Click ‘Google Cloud Storage’ from the sources list and then ‘Create New Connection’. There are two options to connect your data through ‘Private Bucket’ and ‘Public Bucket’.
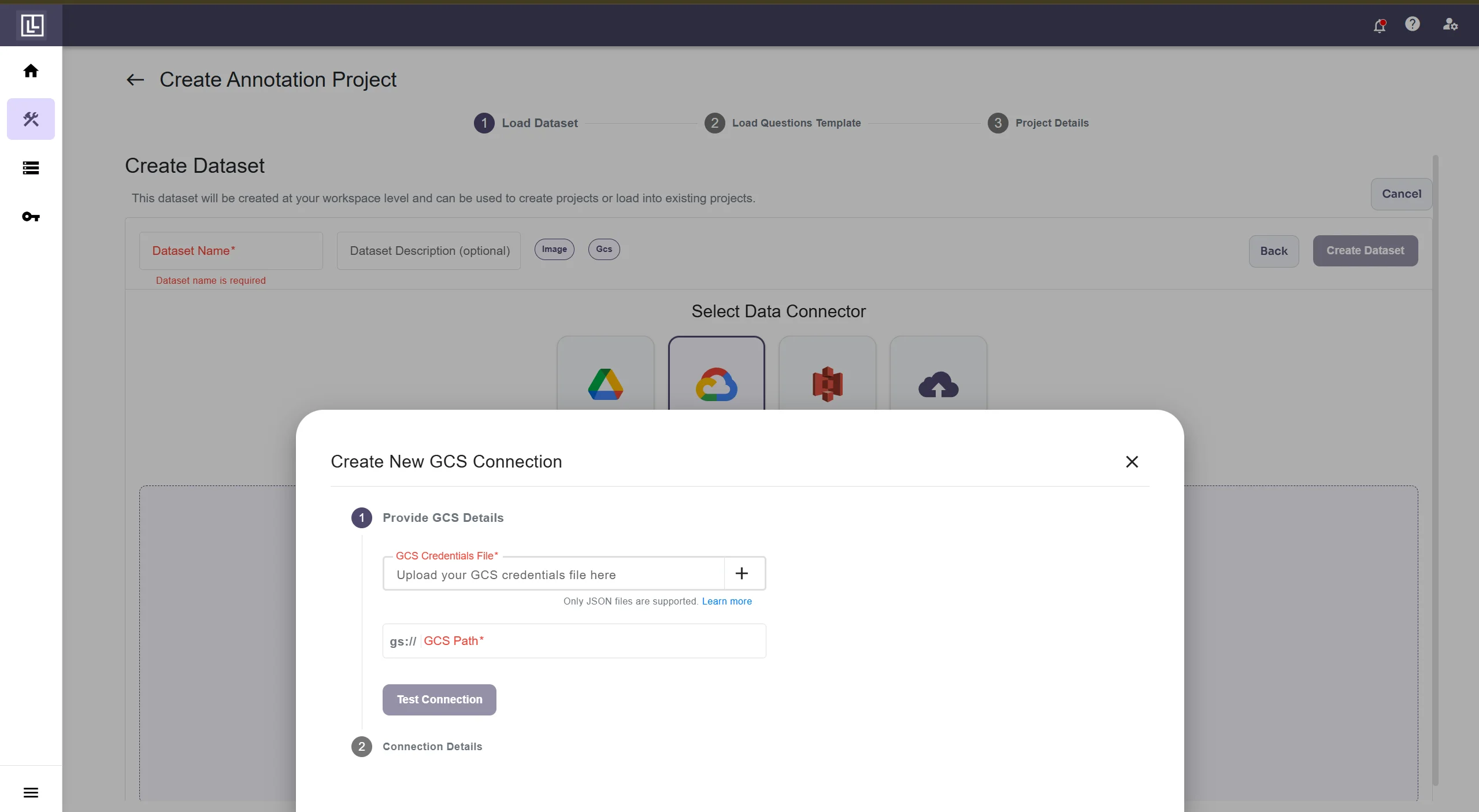 After filling the details successfully, click on Test Connection, if the details are correct, you should see this.
After filling the details successfully, click on Test Connection, if the details are correct, you should see this.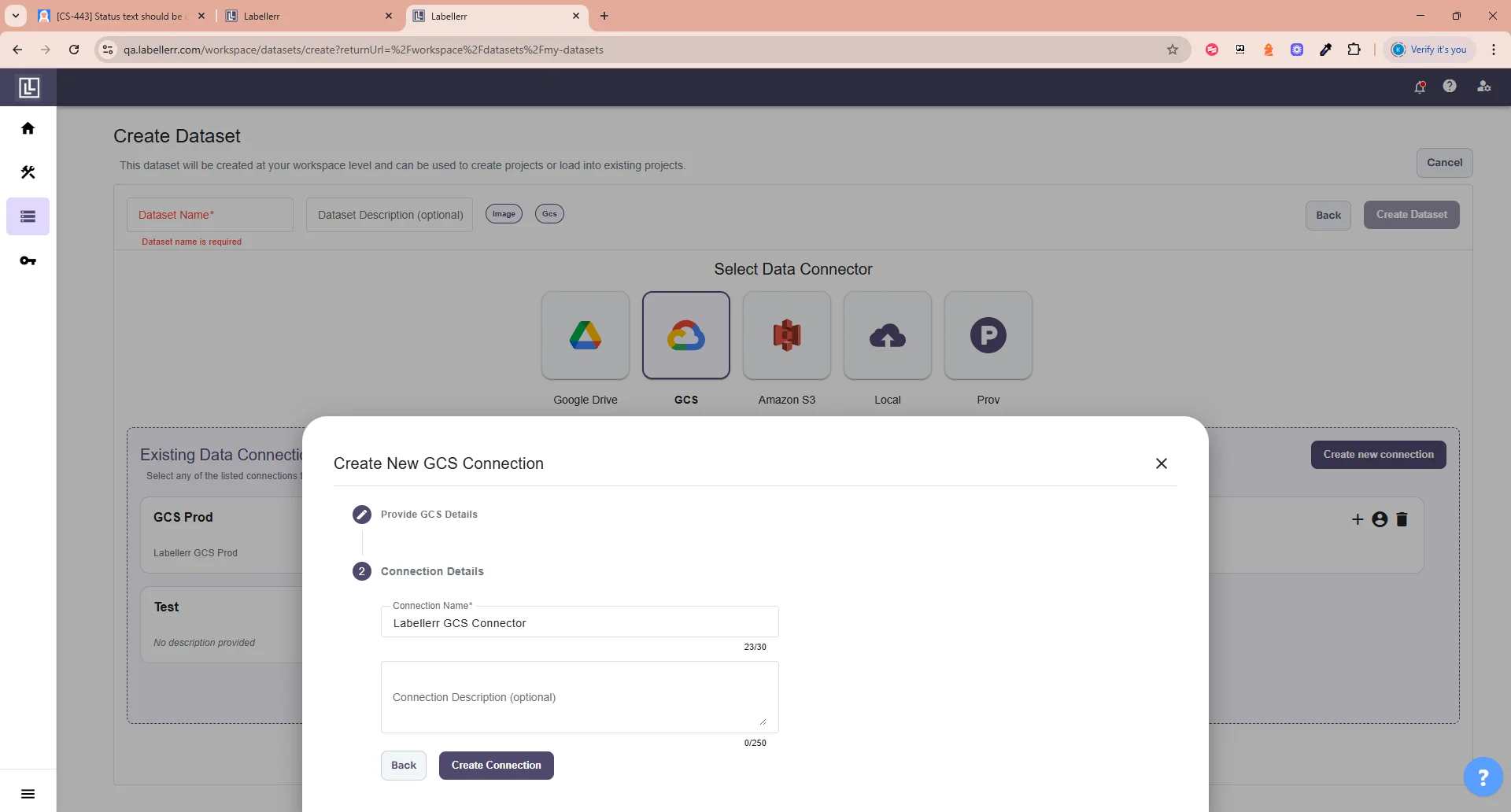 Else you will get this error.
Else you will get this error.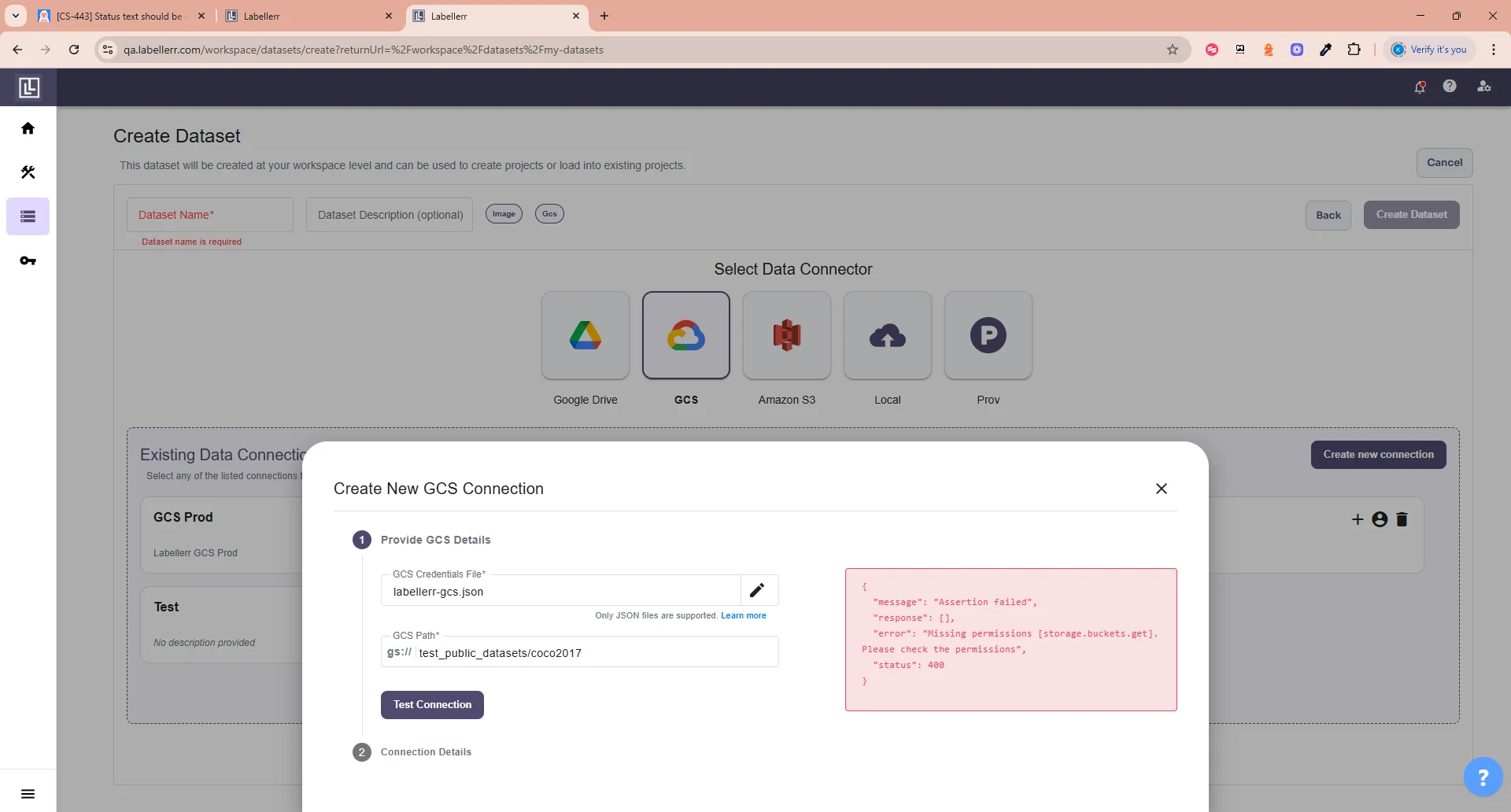 If successfully tested the connection and your files are recognized, you will need to fill the Connection name and Description(Optional).
If successfully tested the connection and your files are recognized, you will need to fill the Connection name and Description(Optional).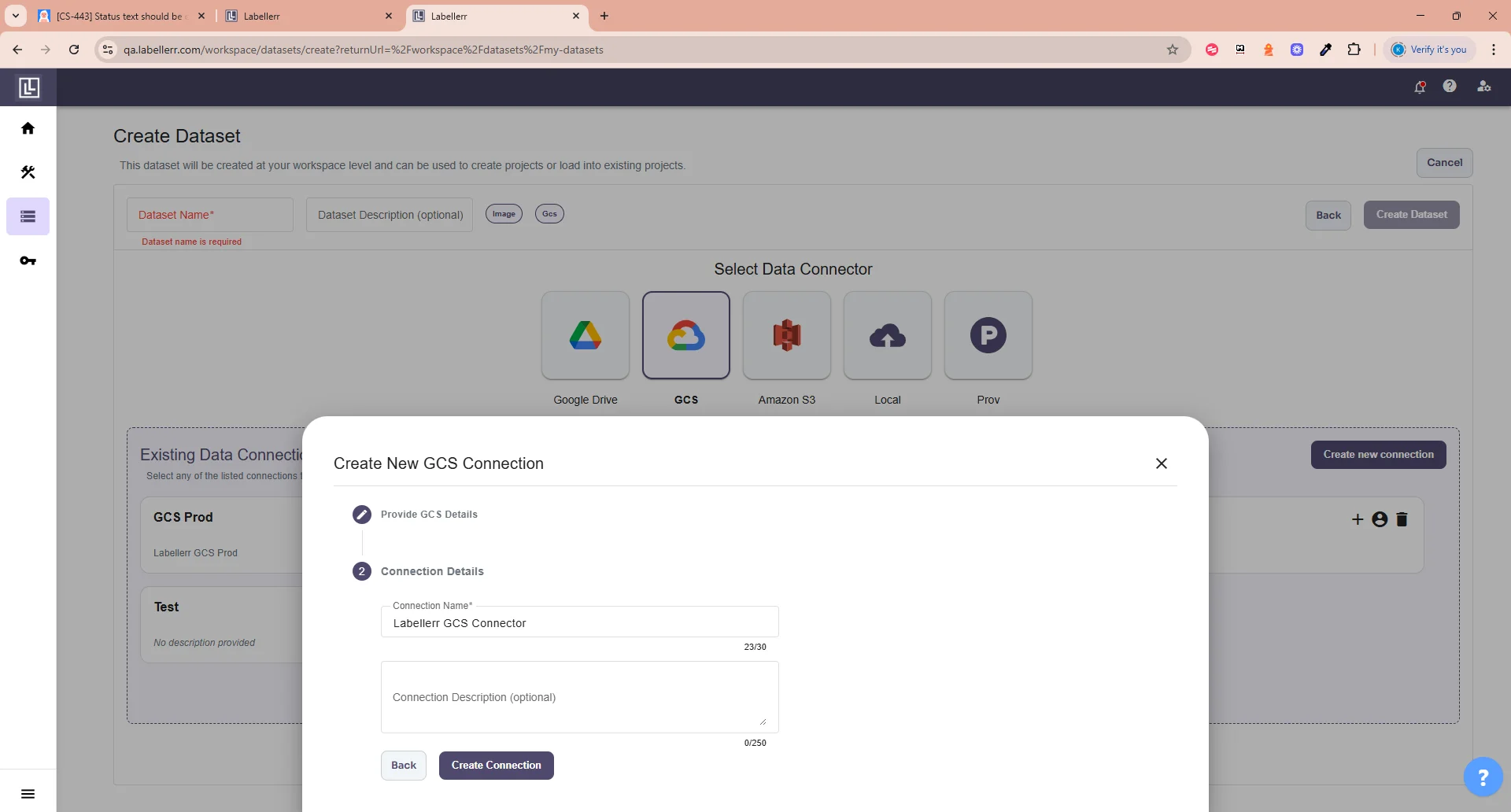





Troubleshooting
Service account JSON is invalid
Service account JSON is invalid
Symptom: Connection test fails with “invalid service account” error.Cause: The JSON key file is corrupted, expired, or incorrectly formatted.Solution:
- Go to IAM & Admin > Service Accounts in Google Cloud Console
- Select your service account
- Click Manage keys
- Delete the old key and create a new one
- Download the new JSON key file and use it for the connection
Permission denied error
Permission denied error
Symptom: Connection test fails with “permission denied” or “403 Forbidden” error.Cause: The service account doesn’t have the required role assigned to the bucket.Solution:
- Go to Cloud Storage > Buckets in Google Cloud Console
- Select your bucket and click Permissions tab
- Click ADD and enter the service account email
- Assign the custom role you created with the required permissions
- Click SAVE
Bucket not found
Bucket not found
Symptom: Connection test fails with “bucket not found” error.Cause: The bucket name in the path doesn’t match the actual bucket name.Solution:
- Verify the gs:// path matches your exact bucket name
- Check for typos in the bucket name
- Ensure the bucket exists in the same Google Cloud project
- Path format should be:
gs://exact-bucket-name/folder/
Dataset creation shows status 500 or 'Failed'
Dataset creation shows status 500 or 'Failed'
Symptom: Dataset appears to create successfully but then shows “Failed” status.Cause: The service account doesn’t have the required permissions to access the GCS bucket.Solution:
- Verify all required permissions are in the custom role
- Ensure the role is assigned to the bucket (not just the project)
- Test the connection before creating datasets:
'No files found with status' during export
'No files found with status' during export
Symptom: Export fails with “No files found with the given status” error.Cause: Files have not been moved to the expected workflow stage.Solution:
- Ensure files have been annotated AND reviewed before exporting
- Check the
statusesparameter in your export configuration - Valid statuses for export:
review,client_review,accepted

